The WPS file format is very similar to the DOC format, it too is a text document but it is created with Microsoft Works Word Processor; and does not include advanced formatting options and macros that a Word document may contain. Most versions of Microsoft Word can open a. 4) Once both the files have been downloaded with the help of prompts, you can open Microsoft Word in order to open the WPS file. 5) Once you are within the MS-Word interface, tap ‘File’, and then tap on ‘Open’. Most versions of Microsoft Word can open a WPS file, as well as Microsoft Publisher. However this format has been discontinued since 2006 and replaced with the standard MS Word DOC format.
Wi-Fi Protected Setup (WPS; originally, Wi-Fi Simple Config) is a network security standard to create a secure wireless home network.
Created by Cisco and introduced in 2003, the point of the protocol is to allow home users who know little of wireless security and may be intimidated by the available security options to set up Wi-Fi Protected Access, as well as making it easy to add new devices to an existing network without entering long passphrases. Wi-Fi Protected Setup allows the owner of Wi-Fi privileges to block other users from using their household Wi-Fi. The owner can also allow people to use Wi-Fi. This can be changed by pressing the WPS button on the home router.[1]
A major security flaw was revealed in December 2011 that affects wireless routers with the WPS PIN feature, which most recent models have enabled by default. The flaw allows a remote attacker to recover the WPS PIN in a few hours with a brute-force attack and, with the WPS PIN, the network's WPA/WPA2 pre-shared key (PSK).[2] Users have been urged to turn off the WPS PIN feature,[3] although this may not be possible on some router models.[4]
Modes[edit]
The standard emphasizes usability and security, and allows four modes in a home network for adding a new device to the network:
- PIN method
- In which a PIN has to be read from either a sticker or display on the new wireless device. This PIN must then be entered at the 'representant' of the network, usually the network's access point. Alternately, a PIN provided by the access point may be entered into the new device. This method is the mandatory baseline mode and everything must support it. The Wi-Fi Direct specification supersedes this requirement by stating that all devices with a keypad or display must support the PIN method.[5]
- Push button method
- In which the user has to push a button, either an actual or virtual one, on both the access point and the new wireless client device. On most devices, this discovery mode turns itself off as soon as a connection is established or after a delay (typically 2 minutes or less), whichever comes first, thereby minimizing its vulnerability. Support of this mode is mandatory for access points and optional for connecting devices. The Wi-Fi Direct specification supersedes this requirement by stating that all devices must support the push button method.[6]
- Near-field communication method
- In which the user has to bring the new client close to the access point to allow a near field communication between the devices. NFC Forum–compliant RFID tags can also be used. Support of this mode is optional.
- USB method
- In which the user uses a USB flash drive to transfer data between the new client device and the network's access point. Support of this mode is optional, but deprecated.
The last two modes are usually referred to as out-of-band methods as there is a transfer of information by a channel other than the Wi-Fi channel itself. Only the first two modes are currently[when?] covered by the WPS certification. The USB method has been deprecated and is not part of the Alliance's certification testing.
Some wireless access points have a dual-function WPS button, and holding this button down for a shorter or longer time may have other functions, such as factory-reset or toggling WiFi.[7]
Some manufacturers, such as Netgear, use a different logo and/or name for Wi-Fi Protected Setup;[8] the Wi-Fi Alliance recommends the use of the Wi-Fi Protected Setup Identifier Mark on the hardware button for this function.[9]
Technical architecture[edit]
The WPS protocol defines three types of devices in a network:
- Registrar
- A device with the authority to issue and revoke access to a network; it may be integrated into a wireless access point (AP), or provided as a separate device.
- Enrollee
- A client device seeking to join a wireless network.
- AP
- An access point functioning as a proxy between a registrar and an enrollee.
The WPS standard defines three basic scenarios that involve components listed above:
- AP with integrated registrar capabilities configures an enrollee station (STA)
- In this case, the session will run on the wireless medium as a series of EAP request/response messages, ending with the AP disassociating from the STA and waiting for the STA to reconnect with its new configuration (handed to it by the AP just before).
- Registrar STA configures the AP as an enrollee
- This case is subdivided in two aspects: first, the session could occur on either a wired or wireless medium, and second, the AP could already be configured by the time the registrar found it. In the case of a wired connection between the devices, the protocol runs over Universal Plug and Play (UPnP), and both devices will have to support UPnP for that purpose. When running over UPnP, a shortened version of the protocol is run (only two messages) as no authentication is required other than that of the joined wired medium. In the case of a wireless medium, the session of the protocol is very similar to the internal registrar scenario, but with opposite roles. As to the configuration state of the AP, the registrar is expected to ask the user whether to reconfigure the AP or keep its current settings, and can decide to reconfigure it even if the AP describes itself as configured. Multiple registrars should have the ability to connect to the AP. UPnP is intended to apply only to a wired medium, while actually it applies to any interface to which an IP connection can be set up. Thus, having manually set up a wireless connection, the UPnP can be used over it in the same manner as with the wired connection.
- Registrar STA configures enrollee STA
- In this case the AP stands in the middle and acts as an authenticator, meaning it only proxies the relevant messages from side to side.
Protocol[edit]
The WPS protocol consists of a series of EAP message exchanges that are triggered by a user action, relying on an exchange of descriptive information that should precede that user's action. The descriptive information is transferred through a new Information Element (IE) that is added to the beacon, probe response, and optionally to the probe request and association request/response messages. Other than purely informative type-length-values, those IEs will also hold the possible and the currently deployed configuration methods of the device.
After this communication of the device capabilities from both ends, the user initiates the actual protocol session. The session consists of eight messages that are followed, in the case of a successful session, by a message to indicate that the protocol is completed. The exact stream of messages may change when configuring different kinds of devices (AP or STA), or when using different physical media (wired or wireless).
Band or radio selection[edit]
Some devices with dual-band wireless network connectivity do not allow the user to select the 2.4 GHz or 5 GHz band (or even a particular radio or SSID) when using Wi-Fi Protected Setup, unless the wireless access point has separate WPS button for each band or radio; however, a number of later wireless routers with multiple frequency bands and/or radios allow the establishment of a WPS session for a specific band and/or radio for connection with clients which cannot have the SSID or band (e.g., 2.4/5 GHz) explicitly selected by the user on the client for connection with WPS (e.g. pushing the 5 GHz, where supported, WPS button on the wireless router will force a client device to connect via WPS on only the 5 GHz band after a WPS session has been established by the client device which cannot explicitly allow the selection of wireless network and/or band for the WPS connection method).[10][11]
Vulnerabilities[edit]
Online brute-force attack[edit]
In December 2011, researcher Stefan Viehböck reported a design and implementation flaw that makes brute-force attacks against PIN-based WPS feasible to be performed on WPS-enabled Wi-Fi networks. A successful attack on WPS allows unauthorized parties to gain access to the network, and the only effective workaround is to disable WPS.[3] The vulnerability centers around the acknowledgement messages sent between the registrar and enrollee when attempting to validate a PIN, which is an eight-digit number used to add new WPA enrollees to the network. Since the last digit is a checksum of the previous digits,[12] there are seven unknown digits in each PIN, yielding 107 = 10,000,000 possible combinations.
When an enrollee attempts to gain access using a PIN, the registrar reports the validity of the first and second halves of the PIN separately. Since the first half of the pin consists of four digits (10,000 possibilities) and the second half has only three active digits (1000 possibilities), at most 11,000 guesses are needed before the PIN is recovered. This is a reduction by three orders of magnitude from the number of PINs that would be required to be tested. As a result, an attack can be completed in under four hours. The ease or difficulty of exploiting this flaw is implementation-dependent, as Wi-Fi router manufacturers could defend against such attacks by slowing or disabling the WPS feature after several failed PIN validation attempts.[2]

A young developer based out of a small town in eastern New Mexico created a tool that exploits this vulnerability to prove that the attack is feasible.[13][14] The tool was then purchased by Tactical Network Solutions in Maryland for 1.5 million dollars. They state that they have known about the vulnerability since early 2011 and had been using it.[15]
In some devices, disabling WPS in the user interface does not result in the feature actually being disabled, and the device remains vulnerable to this attack.[4]Firmware updates have been released for some of these devices allowing WPS to be disabled completely. Vendors could also patch the vulnerability by adding a lock-down period if the Wi-Fi access point detects a brute-force attack in progress, which disables the PIN method for long enough to make the attack impractical.[16]
Offline brute-force attack[edit]
In the summer of 2014, Dominique Bongard discovered what he called the Pixie Dust attack. This attack works only on the default WPS implementation of several wireless chip makers, including Ralink, MediaTek, Realtek and Broadcom. The attack focuses on a lack of randomization when generating the E-S1 and E-S2 'secret' nonces. Knowing these two nonces, the PIN can be recovered within a couple of minutes. A tool called pixiewps has been developed[17] and a new version of Reaver has been developed to automate the process.[18]
Since both the access point and client (enrollee and registrar, respectively) need to prove they know the PIN to make sure the client is not connecting to a rogue AP, the attacker already has two hashes that contain each half of the PIN, and all they need is to brute-force the actual PIN. The access point sends two hashes, E-Hash1 and E-Hash2, to the client, proving that it also knows the PIN. E-Hash1 and E-Hash2 are hashes of (E-S1 | PSK1 | PKe | PKr) and (E-S2 | PSK2 | PKe | PKr), respectively. The hashing function is HMAC-SHA-256 and uses the 'authkey' that is the key used to hash the data.
Physical security issues[edit]
All WPS methods are vulnerable to usage by an unauthorized user if the wireless access point is not kept in a secure area.[19][20][21] Many wireless access points have security information (if it is factory-secured) and the WPS PIN printed on them; this PIN is also often found in the configuration menus of the wireless access point. If this PIN cannot be changed or disabled, the only remedy is to get a firmware update to enable the PIN to be changed, or to replace the wireless access point.
It is possible to extract a wireless passphrase with the following methods using no special tools:[22]
- A wireless passphrase can be extracted using WPS under Windows Vista and newer versions of Windows, under administrative privileges by connecting with this method then bringing up the properties for this wireless network and clicking on 'show characters'.
- A simple exploit in the Intel PROset wireless client utility can reveal the wireless passphrase when WPS is used, after a simple move of the dialog box which asks if you want to reconfigure this access point.[22]
A generic service bulletin regarding physical security for wireless access points.
A wireless router showing printed preset security information including the Wi-Fi Protected Setup PIN.
References[edit]
- ^Higgins, Tim. 'How is WPS supposed to work?'. SmallNetBuilder. Retrieved 2020-05-01.
- ^ abViehböck, Stefan (2011-12-26). 'Brute forcing Wi-Fi Protected Setup'(PDF). Retrieved 2011-12-30.
- ^ abAllar, Jared (2011-12-27). 'Vulnerability Note VU#723755 - WiFi Protected Setup PIN brute force vulnerability'. Vulnerability Notes Database. US CERT. Retrieved 2011-12-31.
- ^ abGallagher, Sean (2012-01-04). 'Hands-on: hacking WiFi Protected Setup with Reaver'. Condé Nast Digital. Retrieved 2012-01-20.
- ^P2P Spec 1.2, clause 3.1.4.3
- ^P2P Spec 1.2,
- ^[1] Tenda W311R+ product page: long press causes factory reset. Retrieved 18 January 2016; Draytek: Vigor 2820 Series manual: short press toggles WiFi
- ^'Netgear N600 Wireless Dual Band Gigabit ADS2+ Modem Router DGND3700 User Manual'(PDF). www.netgear.com. Retrieved January 16, 2016.
- ^'Wi-Fi Alliance Brand Style Guide 2014'(PDF). www.wi-fi.org. Wi-Fi Alliance. April 2014. Retrieved January 16, 2016.
- ^[2] 'D-Link DSL-2544N Dual Band Wireless N600 Gigabit ADSL2+ Modem Router User Manual, Version 1.0', Page 11, Retrieved 26 January 2016.
- ^NetComm NF8AC User Guide, Page 11, http://media.netcomm.com.au/public/assets/pdf_file/0004/142384/NF8AC-User-Guide.pdf , Retrieved October 16, 2016.
- ^'Windows Connect Now–NET (WCN-NET) Specifications'. Microsoft Corporation. 2006-12-08. Retrieved 2011-12-30.
- ^'reaver-wps'. Retrieved 2011-12-30.
- ^'Reaver demonstration on WPS - proof of concept'.
- ^Dennis Fisher (2011-12-29). 'Attack Tool Released for WPS PIN Vulnerability'. Retrieved 2011-12-31.
This is a capability that we at TNS have been testing, perfecting and using for nearly a year.
- ^Slavin, Brad (January 18, 2013). 'Wi-Fi Security – The Rise and Fall of WPS'. Netstumbler.com. Retrieved December 17, 2013.
- ^'pixiewps'. Retrieved 2015-05-05.
- ^'Modified Reaver'. Retrieved 2015-05-05.
- ^'WPS- Advantages and Vulnerability', ComputerHowToGuide.com, September 4, 2014, http://www.computerhowtoguide.com/2014/09/wps-advantages-vulnerability.html , Retrieved October 16, 2016.
- ^'Wi-Fi Protected Setup (WPS) is Insecure: Here’s Why You Should Disable It', How-To-Geek, November 24, 2013, http://www.howtogeek.com/176124/wi-fi-protected-setup-wps-is-insecure-heres-why-you-should-disable-it/ , Retrieved October 16, 2016.
- ^'Wi-Fi Protected Setup: Friend or Foe', Tomáš Rosa, Smart Cards & Devices Forum 2013, May 23, Prague, http://crypto.hyperlink.cz/files/rosa_scadforum13.pdf , Tomáš Rosa, Retrieved October 16, 2016.
- ^ abCherry, Bryce. An Emphasis On Physical Security for Wireless Networks AKA The Dangers Of Wi-Fi Protected Setup https://www.youtube.com/watch?v=kRhyvRAUG6k Retrieved 2014-7-14
External links[edit]
- Wi-Fi Protected Setup Knowledge Center at the Wi-Fi Alliance

For different reasons, you may lose your WPS documents, such as accidental deletion, hard drive formatting, virus attack, and more. Are you facing the situation that you lost a WPS file that was not saved? Do you know how to recover unsaved files in WPS document?
WPS office is an office suite which can be a great alternative to Microsoft Office Suite. It is mainly made up of three primary components, WPS Writer, WPS Presentation, and WPS Spreadsheet. It is compatible with any Microsoft Office files, so you can handily access and edit your files on it.
Recover WPS FileHowever, similar to the Microsoft Office, WPS users may also get the files loss issue. No matter how you lost files in WPS document, you can take the 3 effective solutions below to recover unsaved files in WPS document, or retrieve deleted files from WPS office.
Part 1. Recover Unsaved WPS Documents Through Auto Backup
To prevent the data loss situation due to WPS program or computer crash, formatted drive, virus attack, or other reasons, WPS office is designed with an Auto Backup feature to automatically create backup files at any time. When you want to recover unsaved files in WPS document, you can try making the recovery through it.
Recover unsaved WPS files from the prompt
When you lost a WPS document that was not saved, you can choose to re-launch your WPS program to access the auto-backup files. When you re-open WPS, you will get a pop up prompt. You can easily access and recover unsaved files in WPS document there.
Follow the similar way, and you can recover not saved Word, Excel, etc., from its Auto-save feature.
Recover unsaved WPS documents from backup management
If you find nothing after you re-launch the WPS program, you can choose to recover lost WPS files from local backup file.
Open your WPS software and then choose the Backup Management tab on the drop-down list. Now you can find your lost files from Backup Management panel on the right. Here you are allowed to open and save these WPS documents.
You can also click View Other Backups on the right bottom to see more local files. If you can't find your lost WPS documents in Backup Management, you can try finding them from other backup files.
Part 2. How to Recover Deleted Files in WPS Office
If you still cannot find your unsaved or lost WPS files after trying the method above, you have to rely on some professional WPS document recovering tool to find your missing files back. Here we strongly recommend the powerful Data Recovery for you to recover deleted or unsaved files in WPS office.
4,000,000+ Downloads
Easily find and recover deleted or unsaved files in WPS document.
Restore any frequently-used data like documents, photos, videos, and more.
Retrieve lost WPS documents from PC, Mac, recycle bin, hard drive, memory card, etc.
Support any data loss situation like mistakenly deletion, hard drive damage, and virus attack.
Step 1Double click on the download button above and follow the instructions to free install and launch this WPS documents recovering software on your computer.
Step 2To recover deleted or unsaved files in WPS office, you can choose the Document option. As you can see, this data recovering tool also enables you to restore lost images, videos, emails and more. Then select the hard drive which may carry your lost WPS documents.
Step 3 Click Scan button on the bottom-right to start a Quick Scan on your selected hard drive. This Data Recovery also offers a Deep Scan feature.
Step 4 When the scanning is over, click Document on the left and then preview all your document files on the right. To quickly locate your deleted WPS files, you can rely on the Filter feature.
Step 5 Choose all the WPS files you want to recover and then click the Recover button to start the recovery. Within just a few clicks, you can handily recover your deleted or unsaved files in WPS.
Part 3. How to Recover Deleted Files in WPS Office in Mobile Android
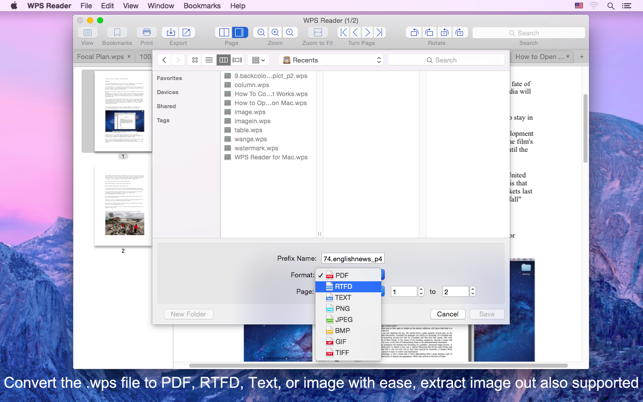
If you are using WPS Office app on your Android device and lost some WPS files, you also need to turn to professional Android data recovery tool. You can use the popular Android Data Recovery to find your lost WPS files back. It has the capability to recover any popular data types including documents, photos, music, messages and more. You can follow the steps below to recover deleted files from WPS office in Android.
Step 1 Double click on the download button above to free install and open this Android Data Recovery on your computer. Connect your Android phone to it with a UBS cable.
Step 2 After connecting successfully, choose the Documents option and then click the Next button.
Step 3 You can see all your Android files are listed in specific data types on the left. Click Documents on the left and then view the detailed information of each file on the right window.
Step 4 Select all the WPS files you want to recover and then click the Recover button to get them back on your computer with ease. When you want to recover deleted Android photos, videos, audio, and more, you can free download it and give it a try.
Part 4. FAQs of WPS Documents Recovery
Question 1. How to recover unsaved Excel files?
To recover unsaved Excel files, you can also rely on the auto-save feature. You can re-open Excel to access your unsaved files.
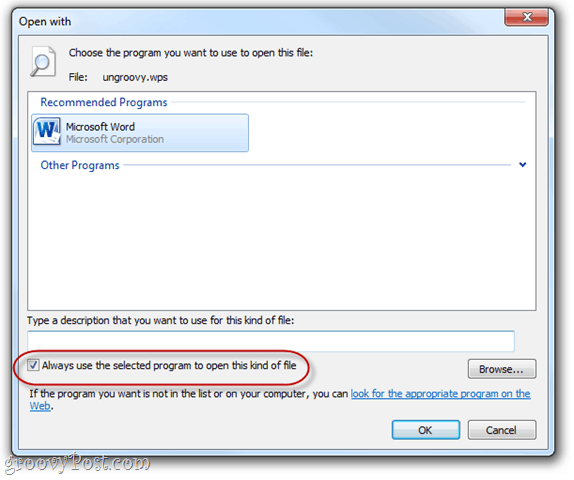
Question 2. How to recover an unsaved Office file?
To easily restore an unsaved Office file, you can click File tab on the top menu bar and then click Open from the drop-down list. Then you can choose the Recent option to access your unsaved files with ease.
Question 3. How to turn on Auto-save in WPS?
Open WPS and click Tool tab and then choose the Option. Go to General and Save and then tick the Recently used file list option. Now you can enable Auto-save feature and set the backup frequency based on your need.
Open Wps Doc
Conclusion
Open Wps In Open Office
How to recover unsaved files in WPS document? You can get 3 simple and effective ways to get your deleted or unsaved WPS files back. If you have any better method to restore lost WPS files, please share it in the comment with other readers.
